CloudRaider: Azure and Google Cloud Platforms Targeted in Ongoing Cloud Credential Stealing Campaign
In June 2023, a malicious actor expanded their cloud credential stealing campaign beyond Amazon Web Services (AWS) to include Azure and Google Cloud Platform (GCP) services.
The campaign, which shares similarities with tools associated with the notorious TeamTNT cryptojacking group, was uncovered by SentinelOne and Permiso. However, attribution in script-based tools remains challenging.
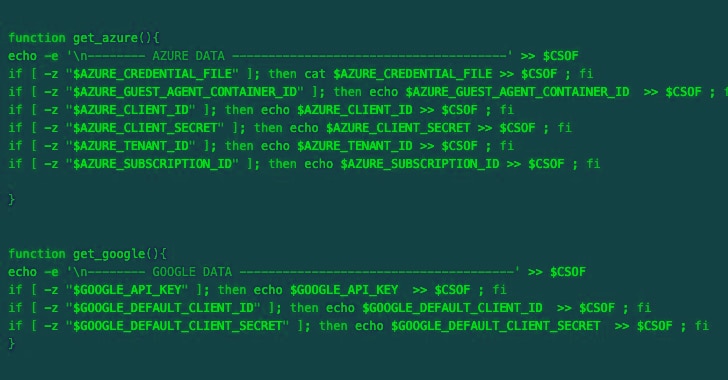
These attacks align with the ongoing Silentbob campaign by TeamTNT, identified by Aqua, which exploits misconfigured cloud services to distribute malware as part of their testing efforts. There are also infrastructure commonalities connecting the SCARLETEEL attacks to this threat actor.
TeamTNT is actively scanning for credentials across multiple cloud environments, including AWS, Azure, and GCP, focusing on public-facing Docker instances. The attacker deploys a worm-like propagation module to compromise these instances. This campaign is an evolution of their intrusion set that previously targeted Jupyter Notebooks in December 2022.
The credential harvesting script has undergone multiple versions between June 15, 2023, and July 11, 2023, suggesting an evolving and active campaign. The newer versions are designed to collect credentials from various services, including AWS, Azure, GCP, Censys, Docker, Filezilla, Git, Grafana, Kubernetes, Linux, Ngrok, PostgreSQL, Redis, S3QL, and SMB. These credentials are then sent to a remote server under the attacker’s control.
SentinelOne researchers noted similarities between the credential collection logic and file targets in this campaign and a Kubelet-targeting campaign previously conducted by TeamTNT in September 2022.
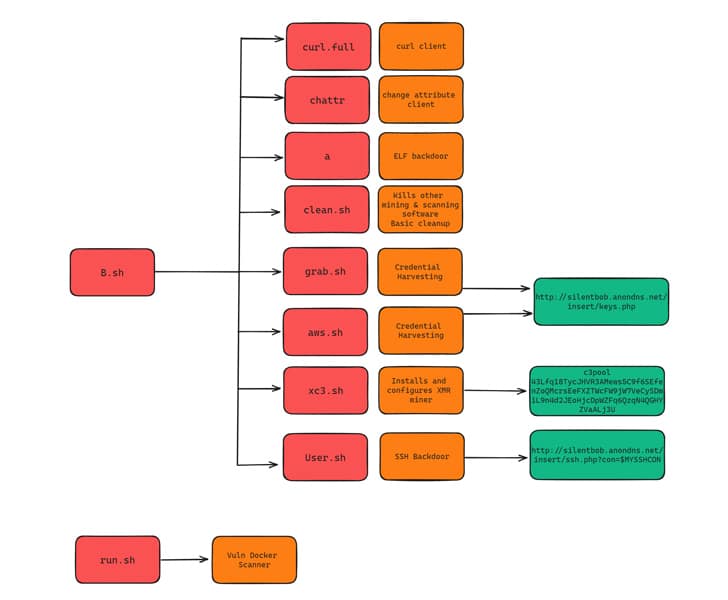
In addition to the shell script malware, the threat actor distributes a Golang-based ELF binary that acts as a scanner to propagate the malware further. The binary also drops a Golang network scanning utility known as Zgrab.
The campaign showcases the expertise of a seasoned cloud actor with familiarity across various technologies. The attention to detail and continuous improvement of tools indicate significant trial and error experiences.
Connections between SCARLETEEL and TeamTNT campaigns have emerged, with similarities observed in techniques and the use of a common Monero wallet address for crypto mining. However, due to certain differences in tactics, techniques, and procedures (TTPs), clear-cut attribution to TeamTNT remains challenging.
While there is overlap in infrastructure usage, accurate attribution to a single threat actor is complex, according to Sysdig. The use of a custom AWS endpoint distinguishes the SCARLETEEL campaign from other observed TTPs.
Đăng ký liền tay Nhận Ngay Bài Mới
Subscribe ngay
Cám ơn bạn đã đăng ký !
Lỗi đăng ký !









Add Comment